前言¶
tcpdump 是我们常用的一个网络抓包工具,它的功能非常的强大。但是它还缺少一个大家反馈很久却一直没实现的一个特性, 那就是:在结果中包含/显示发送网络请求/流量的进程信息,以及支持抓取指定进程的网络流量。
当前针对 tcpdump 抓取的流量信息,如果要获取对应的进程信息的话,常见的方法是: 基于请求的连接信息,通过 ss 或 netstat 之内的工具反查进程信息。 这个方法的缺点是:操作起来比较繁琐以及无法查找匹配短生命周期的进程所发送的网络流量。
至于基于 tcpdump 实现抓取指定进程的网络流量,常见的方法是:在知晓进程要访问的目标服务地址信息的前提下, 在使用 tcpdump 时按目的地址信息过滤流量; 或者是在特定的网络命名空间中运行目标进程,然后再在该网络命名空间下使用 tcpdump 抓包。 这两个方法的缺点是:需要提前知晓目标进程访问的目的地址或者需要改变目标进程的执行方式,适用场景有限。
本文将介绍一个新的工具 ptcpdump,基于这个工具,我们既可以在抓包时直接感知发送流量的进程信息, 也可以直接对运行中或待运行的任意进程进行网络抓包。如果流量是从容器内的进程发出的话, 它还支持显示流量的容器或 Pod 信息以及对特定容器或 Pod 进行抓包。
ptcpdump 介绍¶
ptcpdump 是一个使用 eBPF 技术开发的、类 tcpdump 的网络抓包工具。 它除了兼容 tcpdump 的常用命令行参数以及包过滤语法外, 还额外提供了如下核心特性:
- 在输出中记录和显示发送网络流量的进程、容器、Pod 信息。
- 支持对指定进程、容器以及 Pod 进行抓包。
- 支持将抓取的数据包保存为 pcapng 格式,可以使用 tcpdump 或者 Wireshark 做进一步分析。
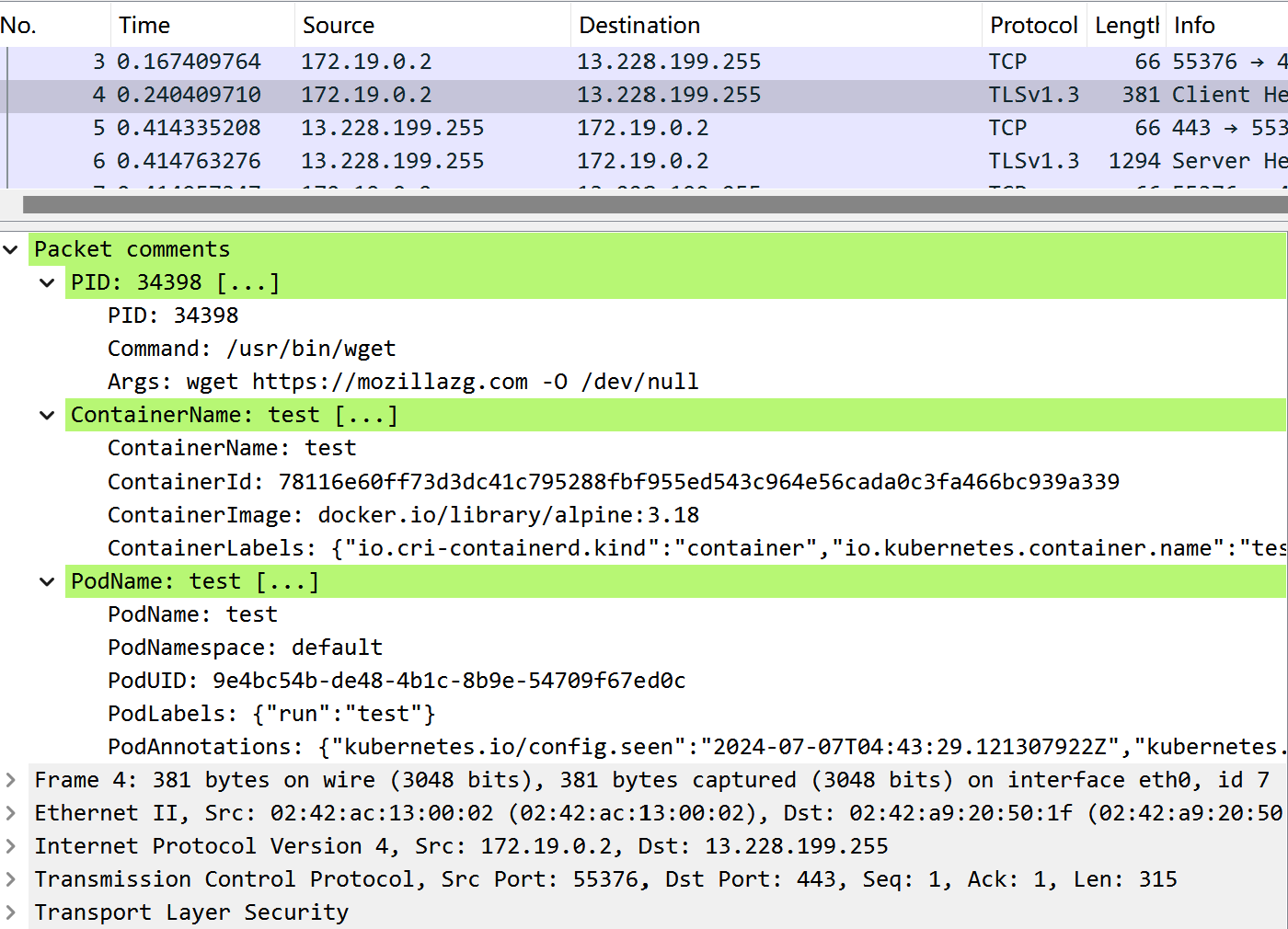
- 当在 Wireshark 中打开保存的 pcapng 文件时,将能够看到每个数据包对应的进程、容器、Pod 信息。
- 使用静态链接的方式编译该工具,系统中不需要安装额外的系统链接库。
更多信息请参考项目的源代码仓库: https://github.com/mozillazg/ptcpdump
下面将以示例的形式介绍 ptcpdump 的核心功能。
兼容 tcpdump 的常用命令行参数和包过滤语法¶
ptcpdump 兼容 tcpdump 的包过滤语法和常用的命令行参数,比如:
sudo tcpdump -i eth0 tcp sudo tcpdump -i eth0 -A -v tcp and port 80 and host 10.10.1.1 sudo tcpdump -i eth0 'tcp[tcpflags] & (tcp-syn|tcp-fin) != 0' sudo tcpdump -i any sudo tcpdump -i any -s 0 -n -c 100 -w demo.pcapng port 80
上面这些常见的 tcpdump 命令可以直接无缝替换为对应的 ptcpdump 命令,只需要将 tcpdump 改为 ptcpdump 即可:
sudo ptcpdump -i eth0 tcp sudo ptcpdump -i eth0 -A -v tcp and port 80 and host 10.10.1.1 sudo ptcpdump -i eth0 'tcp[tcpflags] & (tcp-syn|tcp-fin) != 0' sudo ptcpdump -i any sudo ptcpdump -i any -s 0 -n -c 100 -w demo.pcapng port 80
在输出中记录和显示发送网络流量的进程、容器和 Pod 信息¶
默认情况下,ptcpdump 将在输出中显示简单的进程、容器以及 Pod 信息:
$ sudo ptcpdump -i any -c 4 port 80 or port 443 2024-07-07 12:56:56 WARN ptcpdump: verbose output suppressed, use -v[v]... for verbose output 2024-07-07 12:56:56 WARN capturing on any, link-type EN10MB (Ethernet), snapshot length 262144 bytes 12:56:59.517657 veth18618a4a wget.13626 In IP 10.244.0.4.46834 > 13.251.96.10.443: Flags [S], seq 2743105662, win 64240, length 0, Container [test], Pod [test.default] 12:56:59.517836 eth0 wget.13626 Out IP 172.19.0.2.46834 > 13.251.96.10.443: Flags [S], seq 2743105662, win 64240, length 0, Container [test], Pod [test.default] 12:56:59.692593 eth0 wget.13626 In IP 13.251.96.10.443 > 172.19.0.2.46834: Flags [S.], seq 1966397178, ack 2743105663, win 65084, length 0, Container [test], Pod [test.default] 12:56:59.692754 veth18618a4a wget.13626 Out IP 13.251.96.10.443 > 10.244.0.4.46834: Flags [S.], seq 1966397178, ack 2743105663, win 65084, length 0, Container [test], Pod [test.default] 4 packets captured 6 packets received by filter 0 packets dropped by kernel
可以通过指定 -v 参数,查看更详细的进程、容器以及 Pod 信息:
$ ptcpdump -i any -c 4 -v port 80 or port 443
2024-07-07 12:58:59 WARN ptcpdump: capturing on any, link-type EN10MB (Ethernet), snapshot length 262144 bytes
12:59:02.265356 veth18618a4a In IP (tos 0x0, ttl 64, id 35996, offset 0, flags [DF], proto TCP (6), length 60)
10.244.0.4.41666 > 13.215.144.61.443: Flags [S], cksum 0xa93a, seq 40651020, win 64240, options [mss 1460,sackOK,TS val 2665081987 ecr 0,nop,wscale 7], length 0
Process (pid 14565, cmd /usr/bin/wget, args wget https://mozillazg.com -O /dev/null)
Container (name test, id 78116e60ff73d3dc41c795288fbf955ed543c964e56cada0c3fa466bc939a339, image docker.io/library/alpine:3.18, labels {"io.cri-containerd.kind":"container","io.kubernetes.container.name":"test","io.kubernetes.pod.name":"test","io.kubernetes.pod.namespace":"default","io.kubernetes.pod.uid":"9e4bc54b-de48-4b1c-8b9e-54709f67ed0c"})
Pod (name test, namespace default, UID 9e4bc54b-de48-4b1c-8b9e-54709f67ed0c, labels {"run":"test"}, annotations {"kubernetes.io/config.seen":"2024-07-07T12:43:29.121307922Z","kubernetes.io/config.source":"api"})
12:59:02.265606 eth0 Out IP (tos 0x0, ttl 63, id 35996, offset 0, flags [DF], proto TCP (6), length 60)
172.19.0.2.41666 > 13.215.144.61.443: Flags [S], cksum 0x4a58, seq 40651020, win 64240, options [mss 1460,sackOK,TS val 2665081987 ecr 0,nop,wscale 7], length 0
Process (pid 14565, cmd /usr/bin/wget, args wget https://mozillazg.com -O /dev/null)
Container (name test, id 78116e60ff73d3dc41c795288fbf955ed543c964e56cada0c3fa466bc939a339, image docker.io/library/alpine:3.18, labels {"io.cri-containerd.kind":"container","io.kubernetes.container.name":"test","io.kubernetes.pod.name":"test","io.kubernetes.pod.namespace":"default","io.kubernetes.pod.uid":"9e4bc54b-de48-4b1c-8b9e-54709f67ed0c"})
Pod (name test, namespace default, UID 9e4bc54b-de48-4b1c-8b9e-54709f67ed0c, labels {"run":"test"}, annotations {"kubernetes.io/config.seen":"2024-07-07T12:43:29.121307922Z","kubernetes.io/config.source":"api"})
12:59:02.462586 eth0 In IP (tos 0x4, ttl 47, id 0, offset 0, flags [DF], proto TCP (6), length 60)
13.215.144.61.443 > 172.19.0.2.41666: Flags [S.], cksum 0x9772, seq 3160052321, ack 40651021, win 65084, options [mss 1240,sackOK,TS val 3710435767 ecr 2665081987,nop,wscale 9], length 0
Process (pid 14565, cmd /usr/bin/wget, args wget https://mozillazg.com -O /dev/null)
Container (name test, id 78116e60ff73d3dc41c795288fbf955ed543c964e56cada0c3fa466bc939a339, image docker.io/library/alpine:3.18, labels {"io.cri-containerd.kind":"container","io.kubernetes.container.name":"test","io.kubernetes.pod.name":"test","io.kubernetes.pod.namespace":"default","io.kubernetes.pod.uid":"9e4bc54b-de48-4b1c-8b9e-54709f67ed0c"})
Pod (name test, namespace default, UID 9e4bc54b-de48-4b1c-8b9e-54709f67ed0c, labels {"run":"test"}, annotations {"kubernetes.io/config.seen":"2024-07-07T12:43:29.121307922Z","kubernetes.io/config.source":"api"})
12:59:02.462782 veth18618a4a Out IP (tos 0x4, ttl 46, id 0, offset 0, flags [DF], proto TCP (6), length 60)
13.215.144.61.443 > 10.244.0.4.41666: Flags [S.], cksum 0x3890, seq 3160052321, ack 40651021, win 65084, options [mss 1240,sackOK,TS val 3710435767 ecr 2665081987,nop,wscale 9], length 0
Process (pid 14565, cmd /usr/bin/wget, args wget https://mozillazg.com -O /dev/null)
Container (name test, id 78116e60ff73d3dc41c795288fbf955ed543c964e56cada0c3fa466bc939a339, image docker.io/library/alpine:3.18, labels {"io.cri-containerd.kind":"container","io.kubernetes.container.name":"test","io.kubernetes.pod.name":"test","io.kubernetes.pod.namespace":"default","io.kubernetes.pod.uid":"9e4bc54b-de48-4b1c-8b9e-54709f67ed0c"})
Pod (name test, namespace default, UID 9e4bc54b-de48-4b1c-8b9e-54709f67ed0c, labels {"run":"test"}, annotations {"kubernetes.io/config.seen":"2024-07-07T12:43:29.121307922Z","kubernetes.io/config.source":"api"})
4 packets captured
6 packets received by filter
0 packets dropped by kernel
通过 -A 参数以 ASCII 格式输出:
14:44:34.457504 ens33 curl.205562 Out IP 10.0.2.15.39984 > 139.178.84.217.80: Flags [P.], seq 2722472188:2722472262, ack 892036871, win 64240, length 74, ParentProc [bash.180205] E..r.,@.@.o. .....T..0.P.E..5+g.P.......GET / HTTP/1.1 Host: kernel.org User-Agent: curl/7.81.0 Accept: */*
通过 -x 参数以 16 进制格式输出:
14:44:34.457504 ens33 curl.205562 IP 10.0.2.15.39984 > 139.178.84.217.80: Flags [P.], seq 2722472188:2722472262, ack 892036871, win 64240, length 74, ParentProc [bash.180205]
0x0000: 4500 0072 de2c 4000 4006 6fbf 0a00 020f
0x0010: 8bb2 54d9 9c30 0050 a245 a0fc 352b 6707
0x0020: 5018 faf0 ecfe 0000 4745 5420 2f20 4854
0x0030: 5450 2f31 2e31 0d0a 486f 7374 3a20 6b65
0x0040: 726e 656c 2e6f 7267 0d0a 5573 6572 2d41
0x0050: 6765 6e74 3a20 6375 726c 2f37 2e38 312e
0x0060: 300d 0a41 6363 6570 743a 202a 2f2a 0d0a
0x0070: 0d0a
通过 -X 参数以 16 进制和 ASCII 格式输出:
14:44:34.457504 ens33 curl.205562 IP 10.0.2.15.39984 > 139.178.84.217.80: Flags [P.], seq 2722472188:2722472262, ack 892036871, win 64240, length 74, ParentProc [bash.180205]
0x0000: 4500 0072 de2c 4000 4006 6fbf 0a00 020f E..r.,@.@.o.....
0x0010: 8bb2 54d9 9c30 0050 a245 a0fc 352b 6707 ..T..0.P.E..5+g.
0x0020: 5018 faf0 ecfe 0000 4745 5420 2f20 4854 P.......GET / HT
0x0030: 5450 2f31 2e31 0d0a 486f 7374 3a20 6b65 TP/1.1..Host: ke
0x0040: 726e 656c 2e6f 7267 0d0a 5573 6572 2d41 rnel.org..User-A
0x0050: 6765 6e74 3a20 6375 726c 2f37 2e38 312e gent: curl/7.81.
0x0060: 300d 0a41 6363 6570 743a 202a 2f2a 0d0a 0..Accept: */*..
0x0070: 0d0a ..
支持对指定进程、容器或 Pod 进行抓包¶
指定进程 pid 抓包¶
可以通过 --pid 参数指定要抓包的进程 pid,实现对指定进程进行抓包:
$ sudo ptcpdump -i any -c 4 --pid 82106 2024-07-07 13:11:40 WARN ptcpdump: verbose output suppressed, use -v[v]... for verbose output 2024-07-07 13:11:40 WARN capturing on any, link-type EN10MB (Ethernet), snapshot length 262144 bytes 13:11:50.170538 ens33 python3.10.82106 Out IP 10.0.2.15.36648 > 13.251.96.10.443: Flags [S], seq 1633417447, win 64240, length 0 13:11:50.369972 ens33 python3.10.82106 In IP 13.251.96.10.443 > 10.0.2.15.36648: Flags [S.], seq 1793291274, ack 1633417448, win 64240, length 0 2 packets captured 3 packets received by filter 0 packets dropped by kernel
同时还可以通过指定 -f 参数对该进程创建的子进程也进行抓包:
$ sudo ptcpdump -i any -c 4 --pid 82106 -f 'tcp[tcpflags] & tcp-fin != 0' 2024-07-07 13:17:31 WARN ptcpdump: verbose output suppressed, use -v[v]... for verbose output 2024-07-07 13:17:31 WARN capturing on any, link-type EN10MB (Ethernet), snapshot length 262144 bytes 13:17:37.800903 ens33 python3.10.82106 Out IP 10.0.2.15.38576 > 52.74.166.77.443: Flags [F.], seq 2442149577, ack 367271121, win 62780, length 0 13:17:37.977316 ens33 python3.10.82106 In IP 52.74.166.77.443 > 10.0.2.15.38576: Flags [FP.], seq 367271145, ack 2442149578, win 64239, length 0 13:17:44.390627 ens33 curl.95920 Out IP 10.0.2.15.38590 > 52.74.166.77.443: Flags [F.], seq 3726932781, ack 1510095004, win 63045, length 0 13:17:44.564990 ens33 curl.95920 In IP 52.74.166.77.443 > 10.0.2.15.38590: Flags [FP.], seq 1510095028, ack 3726932782, win 64239, length 0 4 packets captured 4 packets received by filter 0 packets dropped by kernel
指定进程名称抓包¶
可以通过 --pname 参数指定进程名称(comm),实现指定进程名称抓包:
$ sudo ptcpdump -i any -c 2 --pname curl 2024-07-07 13:23:18 WARN ptcpdump: verbose output suppressed, use -v[v]... for verbose output 2024-07-07 13:23:18 WARN capturing on any, link-type EN10MB (Ethernet), snapshot length 262144 bytes 13:23:24.881499 lo curl.26511 Out IP 127.0.0.1.43332 > 127.0.0.53.53: 44133+ [1au] A? mozillazg.com. (42) 13:23:24.881663 lo curl.26511 Out IP 127.0.0.1.43332 > 127.0.0.53.53: 14694+ [1au] AAAA? mozillazg.com. (42) 2 packets captured 2 packets received by filter 0 packets dropped by kernel
通过运行目标程序来抓包¶
有需要的话,也可以通过使用 -- 参数运行目标程序的方式来实现对特定程序进行抓包:
$ sudo ptcpdump -i any -- curl -I https://mozillazg.com 2024-07-07 13:26:44 WARN ptcpdump: verbose output suppressed, use -v[v]... for verbose output 2024-07-07 13:26:44 WARN capturing on any, link-type EN10MB (Ethernet), snapshot length 262144 bytes 13:26:44.055757 lo curl.28094 Out IP 127.0.0.1.48826 > 127.0.0.53.53: 8942+ [1au] A? mozillazg.com. (42) 13:26:44.055914 lo curl.28094 Out IP 127.0.0.1.48826 > 127.0.0.53.53: 34274+ [1au] AAAA? mozillazg.com. (42) 13:26:44.775840 lo curl.28094 In IP 127.0.0.53.53 > 127.0.0.1.48826: 8942 3/0/1 CNAME mozillazg.netlify.com., A 13.251.96.10, A 46.137.195.11 (106) 13:26:45.135988 lo curl.28094 In IP 127.0.0.53.53 > 127.0.0.1.48826: 34274 3/0/1 CNAME mozillazg.netlify.com., AAAA 2406:da18:880:3802::c8, AAAA 2406:da18:b3d:e202::64 (130) 13:26:45.136819 wlp4s0 curl.28094 Out IP6 2409:8a00:2631:22f0:acdc:55a6:9015:b8f1.53744 > 2406:da18:880:3802::c8.443: Flags [S], seq 3460683104, win 64800, length 0 13:26:45.310505 wlp4s0 curl.28094 In IP6 2406:da18:880:3802::c8.443 > 2409:8a00:2631:22f0:acdc:55a6:9015:b8f1.53744: Flags [S.], seq 630810442, ack 3460683105, win 65232, length 0 13:26:45.310821 wlp4s0 curl.28094 Out IP6 2409:8a00:2631:22f0:acdc:55a6:9015:b8f1.53744 > 2406:da18:880:3802::c8.443: Flags [.], seq 3460683105, ack 630810443, win 507, length 0 13:26:45.414551 wlp4s0 curl.28094 Out IP6 2409:8a00:2631:22f0:acdc:55a6:9015:b8f1.53744 > 2406:da18:880:3802::c8.443: Flags [P.], seq 3460683105:3460683622, ack 630810443, win 507, length 517 13:26:45.595214 wlp4s0 curl.28094 In IP6 2406:da18:880:3802::c8.443 > 2409:8a00:2631:22f0:acdc:55a6:9015:b8f1.53744: Flags [.], seq 630810443, ack 3460683622, win 127, length 0 13:26:45.595413 wlp4s0 curl.28094 In IP6 2406:da18:880:3802::c8.443 > 2409:8a00:2631:22f0:acdc:55a6:9015:b8f1.53744: Flags [.], seq 630810443:630811651, ack 3460683622, win 127, length 1208 13:26:45.595595 wlp4s0 curl.28094 Out IP6 2409:8a00:2631:22f0:acdc:55a6:9015:b8f1.53744 > 2406:da18:880:3802::c8.443: Flags [.], seq 3460683622, ack 630811651, win 501, length 0 13:26:45.595702 wlp4s0 curl.28094 In IP6 2406:da18:880:3802::c8.443 > 2409:8a00:2631:22f0:acdc:55a6:9015:b8f1.53744: Flags [P.], seq 630811651:630812859, ack 3460683622, win 127, length 1208 13:26:45.595797 wlp4s0 curl.28094 Out IP6 2409:8a00:2631:22f0:acdc:55a6:9015:b8f1.53744 > 2406:da18:880:3802::c8.443: Flags [.], seq 3460683622, ack 630812859, win 492, length 0 13:26:45.595862 wlp4s0 curl.28094 In IP6 2406:da18:880:3802::c8.443 > 2409:8a00:2631:22f0:acdc:55a6:9015:b8f1.53744: Flags [P.], seq 630812859:630813338, ack 3460683622, win 127, length 479 13:26:45.595934 wlp4s0 curl.28094 Out IP6 2409:8a00:2631:22f0:acdc:55a6:9015:b8f1.53744 > 2406:da18:880:3802::c8.443: Flags [.], seq 3460683622, ack 630813338, win 489, length 0 13:26:45.600998 wlp4s0 curl.28094 Out IP6 2409:8a00:2631:22f0:acdc:55a6:9015:b8f1.53744 > 2406:da18:880:3802::c8.443: Flags [P.], seq 3460683622:3460683686, ack 630813338, win 489, length 64 13:26:45.601344 wlp4s0 curl.28094 Out IP6 2409:8a00:2631:22f0:acdc:55a6:9015:b8f1.53744 > 2406:da18:880:3802::c8.443: Flags [P.], seq 3460683686:3460683781, ack 630813338, win 489, length 95 13:26:45.616759 wlp4s0 curl.28094 Out IP6 2409:8a00:2631:22f0:acdc:55a6:9015:b8f1.53744 > 2406:da18:880:3802::c8.443: Flags [P.], seq 3460683781:3460683882, ack 630813338, win 501, length 101 13:26:45.779516 wlp4s0 curl.28094 In IP6 2406:da18:880:3802::c8.443 > 2409:8a00:2631:22f0:acdc:55a6:9015:b8f1.53744: Flags [.], seq 630813338, ack 3460683781, win 127, length 0 13:26:45.779792 wlp4s0 curl.28094 In IP6 2406:da18:880:3802::c8.443 > 2409:8a00:2631:22f0:acdc:55a6:9015:b8f1.53744: Flags [P.], seq 630813338:630813399, ack 3460683781, win 127, length 61 13:26:45.779996 wlp4s0 curl.28094 In IP6 2406:da18:880:3802::c8.443 > 2409:8a00:2631:22f0:acdc:55a6:9015:b8f1.53744: Flags [P.], seq 630813399:630813443, ack 3460683781, win 127, length 44 13:26:45.780318 wlp4s0 curl.28094 Out IP6 2409:8a00:2631:22f0:acdc:55a6:9015:b8f1.53744 > 2406:da18:880:3802::c8.443: Flags [P.], seq 3460683882:3460683913, ack 630813443, win 501, length 31 HTTP/2 200 13:26:45.788787 wlp4s0 curl.28094 In IP6 2406:da18:880:3802::c8.443 > 2409:8a00:2631:22f0:acdc:55a6:9015:b8f1.53744: Flags [P.], seq 630813443:630813677, ack 3460683882, win 127, length 234 accept-ranges: bytes age: 79059 cache-control: public,max-age=0,must-revalidate cache-status: "Netlify Edge"; hit content-type: text/html; charset=UTF-8 date: Sun, 07 Jul 2024 05:26:44 GMT etag: "80cf37f5974e2232d976c6f622121dee-ssl" server: Netlify strict-transport-security: max-age=31536000 x-nf-request-id: 01J25THACQSN9364YHSR2C0X5F content-length: 11727 13:26:45.789558 wlp4s0 curl.28094 Out IP6 2409:8a00:2631:22f0:acdc:55a6:9015:b8f1.53744 > 2406:da18:880:3802::c8.443: Flags [P.], seq 3460683913:3460683937, ack 630813677, win 501, length 24 13:26:45.791514 wlp4s0 curl.28094 Out IP6 2409:8a00:2631:22f0:acdc:55a6:9015:b8f1.53744 > 2406:da18:880:3802::c8.443: Flags [F.], seq 3460683937, ack 630813677, win 501, length 0 13:26:45.963642 wlp4s0 curl.28094 In IP6 2406:da18:880:3802::c8.443 > 2409:8a00:2631:22f0:acdc:55a6:9015:b8f1.53744: Flags [.], seq 630813677, ack 3460683937, win 127, length 0 13:26:45.963956 wlp4s0 curl.28094 In IP6 2406:da18:880:3802::c8.443 > 2409:8a00:2631:22f0:acdc:55a6:9015:b8f1.53744: Flags [P.], seq 630813677:630813701, ack 3460683937, win 127, length 24 13:26:45.964172 wlp4s0 curl.28094 Out IP6 2409:8a00:2631:22f0:acdc:55a6:9015:b8f1.53744 > 2406:da18:880:3802::c8.443: Flags [R], seq 3460683937, win 0, length 0 13:26:45.964415 wlp4s0 curl.28094 In IP6 2406:da18:880:3802::c8.443 > 2409:8a00:2631:22f0:acdc:55a6:9015:b8f1.53744: Flags [F.], seq 630813701, ack 3460683937, win 127, length 0 13:26:45.964506 wlp4s0 curl.28094 Out IP6 2409:8a00:2631:22f0:acdc:55a6:9015:b8f1.53744 > 2406:da18:880:3802::c8.443: Flags [R], seq 3460683937, win 0, length 0 13:26:45.966158 wlp4s0 curl.28094 In IP6 2406:da18:880:3802::c8.443 > 2409:8a00:2631:22f0:acdc:55a6:9015:b8f1.53744: Flags [.], seq 630813702, ack 3460683938, win 127, length 0 13:26:45.966299 wlp4s0 curl.28094 Out IP6 2409:8a00:2631:22f0:acdc:55a6:9015:b8f1.53744 > 2406:da18:880:3802::c8.443: Flags [R], seq 3460683938, win 0, length 0 32 packets captured 32 packets received by filter 0 packets dropped by kernel
指定容器抓包¶
可以通过 --container-id 参数指定容器 id 进行抓包:
$ sudo ptcpdump -i any -c 2 --container-id 36f0310403b1 2024-07-07 13:36:19 WARN ptcpdump: verbose output suppressed, use -v[v]... for verbose output 2024-07-07 13:36:19 WARN capturing on any, link-type EN10MB (Ethernet), snapshot length 262144 bytes 13:36:24.191242 veth09dec8f curl.32636 In IP 172.19.0.2.48960 > 18.139.194.139.443: Flags [S], seq 3213779351, win 64240, length 0, Container [kind-control-plane] 13:36:24.191369 wlp4s0 curl.32636 Out IP 192.168.1.50.48960 > 18.139.194.139.443: Flags [S], seq 3213779351, win 64240, length 0, Container [kind-control-plane] 2 packets captured 2 packets received by filter 0 packets dropped by kernel
也可以通过 --container-name 参数指定容器名称进行抓包:
$ sudo ptcpdump -i any -c 2 --container-name kind-control-plane 2024-07-07 13:37:16 WARN ptcpdump: verbose output suppressed, use -v[v]... for verbose output 2024-07-07 13:37:16 WARN capturing on any, link-type EN10MB (Ethernet), snapshot length 262144 bytes 13:37:22.560764 veth09dec8f curl.33093 In IP 172.19.0.2.39084 > 18.139.194.139.443: Flags [S], seq 3645727033, win 64240, length 0, Container [kind-control-plane] 13:37:22.561010 wlp4s0 curl.33093 Out IP 192.168.1.50.39084 > 18.139.194.139.443: Flags [S], seq 3645727033, win 64240, length 0, Container [kind-control-plane] 2 packets captured 2 packets received by filter 0 packets dropped by kernel
指定 Pod 抓包¶
可以通过 --pod-name 参数指定 Pod 名称进行抓包, 参数值的格式为 <pod 名称>.<pod 命名空间>:
$ sudo ptcpdump -i any -c 2 --pod-name test.default 2024-07-07 13:38:29 WARN ptcpdump: verbose output suppressed, use -v[v]... for verbose output 2024-07-07 13:38:29 WARN capturing on any, link-type EN10MB (Ethernet), snapshot length 262144 bytes 13:38:34.175752 eth0 wget.33660 Out IP 172.19.0.2.51564 > 13.215.144.61.443: Flags [S], seq 567383917, win 64240, length 0, Container [test], Pod [test.default] 13:38:34.372894 eth0 wget.33660 In IP 13.215.144.61.443 > 172.19.0.2.51564: Flags [S.], seq 2654865684, ack 567383918, win 65084, length 0, Container [test], Pod [test.default] 2 packets captured 3 packets received by filter 0 packets dropped by kernel
将数据保存为 pcapng 格式使用 tcpdump 或 Wireshark 进行分析¶
保存为 pcapng 格式¶
可以通过 -w 参数将抓包数据保存为 pcapng 格式:
$ sudo ptcpdump -i any -c 5 -w demo.pcapng 2024-07-07 13:41:32 WARN ptcpdump: verbose output suppressed, use -v[v]... for verbose output 2024-07-07 13:41:32 WARN capturing on any, link-type EN10MB (Ethernet), snapshot length 262144 bytes 5 packets captured 22 packets received by filter 0 packets dropped by kernel
使用 tcpdump 进行分析¶
可以直接通过管道的方式通过 tcpdump 对抓取的数据进行分析:
$ sudo ptcpdump -i any -c 5 -w - port 80 | tcpdump -n -r - reading from file -, link-type EN10MB (Ethernet), snapshot length 65535 2024-07-07 13:44:33 WARN ptcpdump: verbose output suppressed, use -v[v]... for verbose output 2024-07-07 13:44:33 WARN capturing on any, link-type EN10MB (Ethernet), snapshot length 262144 bytes 13:44:44.530637 IP6 2409:8a00:2631:22f0:acdc:55a6:9015:b8f1.50858 > 2406:da18:880:3801::c8.80: Flags [S], seq 495824072, win 64800, options [mss 1440,sackOK,TS val 2411675580 ecr 0,nop,wscale 7], length 0 13:44:44.708902 IP6 2406:da18:880:3801::c8.80 > 2409:8a00:2631:22f0:acdc:55a6:9015:b8f1.50858: Flags [S.], seq 640438481, ack 495824073, win 65232, options [mss 1220,sackOK,TS val 1591525382 ecr 2411675580,nop,wscale 9], length 0 13:44:44.709261 IP6 2409:8a00:2631:22f0:acdc:55a6:9015:b8f1.50858 > 2406:da18:880:3801::c8.80: Flags [.], ack 1, win 507, options [nop,nop,TS val 2411675670 ecr 1591525382], length 0 13:44:44.709475 IP6 2409:8a00:2631:22f0:acdc:55a6:9015:b8f1.50858 > 2406:da18:880:3801::c8.80: Flags [P.], seq 1:78, ack 1, win 507, options [nop,nop,TS val 2411675670 ecr 1591525382], length 77: HTTP: GET / HTTP/1.1 5 packets captured 6 packets received by filter 0 packets dropped by kernel 13:44:44.877110 IP6 2406:da18:880:3801::c8.80 > 2409:8a00:2631:22f0:acdc:55a6:9015:b8f1.50858: Flags [P.], seq 1:266, ack 78, win 128, options [nop,nop,TS val 1591525469 ecr 2411675670], length 265: HTTP: HTTP/1.1 301 Moved Permanently
也可以通过读取文件的方式通过 tcpdump 对抓取的数据进行分析:
$ tcpdump -n -r demo.pcapng reading from file demo.pcapng, link-type EN10MB (Ethernet), snapshot length 65535 13:47:41.169584 IP6 2409:8a00:2631:22f0:acdc:55a6:9015:b8f1.43038 > 2406:da18:b3d:e201::64.80: Flags [S], seq 3876639697, win 64800, options [mss 1440,sackOK,TS val 2072195434 ecr 0,nop,wscale 7], length 0 13:47:41.571055 IP 192.168.1.50.60580 > 18.139.194.139.80: Flags [S], seq 481256927, win 64240, options [mss 1460,sackOK,TS val 2707199178 ecr 0,nop,wscale 7], length 0 13:47:41.956270 IP6 2406:da18:b3d:e201::64.80 > 2409:8a00:2631:22f0:acdc:55a6:9015:b8f1.43038: Flags [S.], seq 2283576526, ack 3876639698, win 65232, options [mss 1220,sackOK,TS val 4276006323 ecr 2072195434,nop,wscale 9], length 0 13:47:41.956437 IP6 2409:8a00:2631:22f0:acdc:55a6:9015:b8f1.43038 > 2406:da18:b3d:e201::64.80: Flags [.], ack 1, win 507, options [nop,nop,TS val 2072195828 ecr 4276006323], length 0 13:47:41.956733 IP6 2409:8a00:2631:22f0:acdc:55a6:9015:b8f1.43038 > 2406:da18:b3d:e201::64.80: Flags [P.], seq 1:78, ack 1, win 507, options [nop,nop,TS val 2072195828 ecr 4276006323], length 77: HTTP: GET / HTTP/1.1
Comments